| .. | ||
| init | ||
| bom.yaml | ||
| build.sh | ||
| init_maa.yaml | ||
| maa_init.png | ||
| README.md | ||
Sample code for doing Microsoft Azure Attestation in Occlum init
This demo is programming in RUST, based on the Azure provided REST APIs. It provides steps to do SGX quote generation and attestation in Occlum init process and save the attestation token to rootfs.
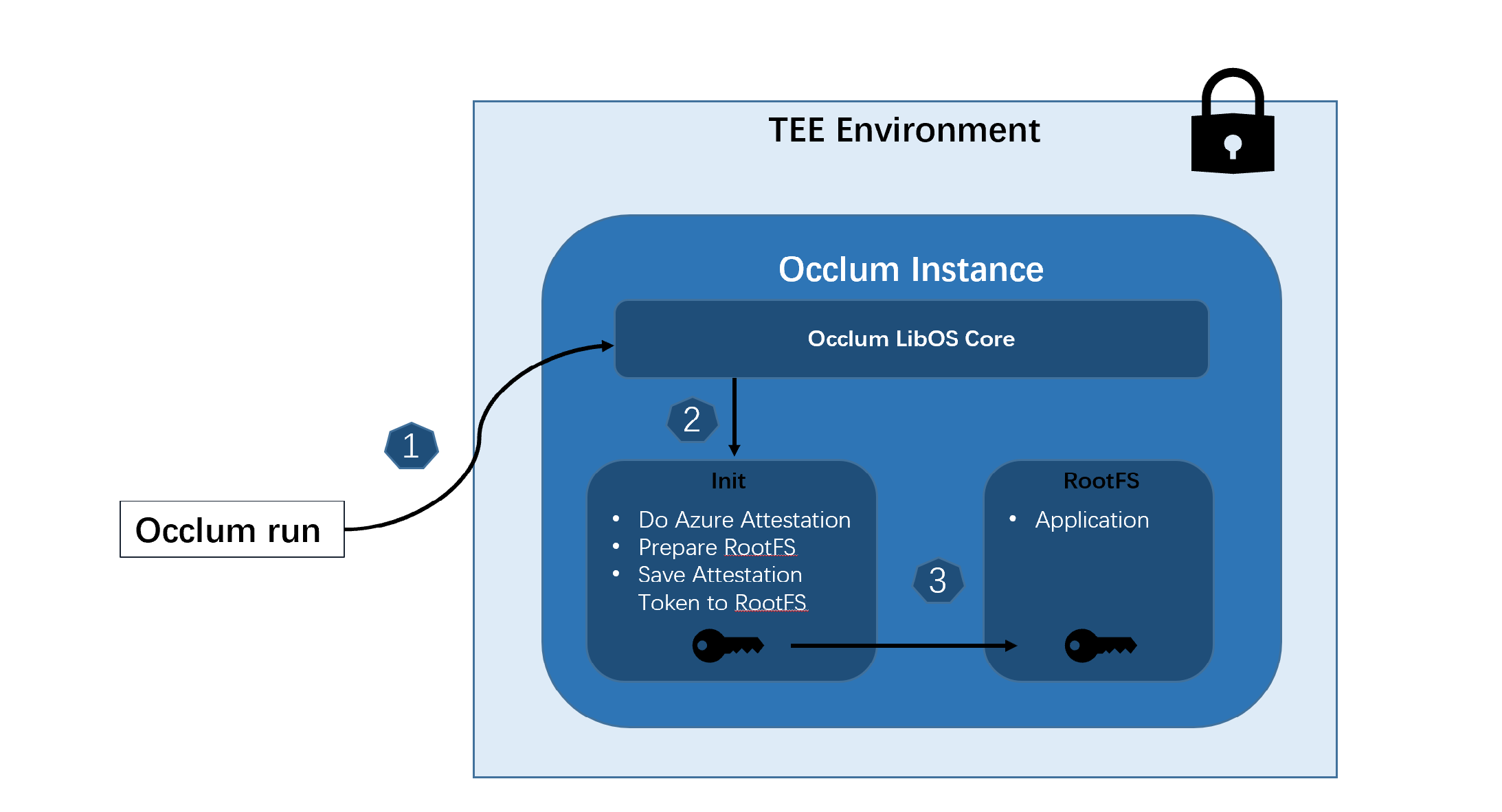
Flow
-
Occlum runto start the Occlum instance. -
For every Occlum instance, it starts
initprocess first, then starts the real application in RootFS. The defaultinitprocess just run RootFS integrity check and then load the RootFS where the real application is located. For this demo, a modifiedinitis used. Besides the generalinitoperation, it does Azure Attestation and saves the token to/root/tokenin RootFS where the real application can access. -
The real application starts with easy access to the Azure Attestation token. The application can set its own strategy for the token. In this demo, a simple
busyboxas real application is used to print the content of attestation token obtained in init process.
Environments
There are three environments below which are provided to users to modify according to the actual scenarios.
-
MAA_PROVIDER_URL The MAA provider URL, this demo uses "https://shareduks.uks.attest.azure.net" In default.
-
MAA_REPORT_DATA The report data (base64 encoded string) to be used for MAA quote generation.
-
MAA_TOKEN_PATH The MAA token and raw quote saved path in rootfs which is
/rootin default. Thus applications could find the attestation response token and raw quote (base64 encoded) in/root/tokenand/root/quote_base64.
Please refer to the scrit for how to modify the above environments.
- Build
- Pull rust-sgx-sdk submodule which is the dependence of occlum dcap library.
# cd occlum
# git submodule update --init
- Do the build with the
scrit.
# ./build.sh
- Run
# cd occlum_instance
# occlum run /bin/busybox cat /root/token
If successful, it prints the Azure attestation token.