| .githooks | ||
| .github | ||
| demos | ||
| deps | ||
| docs | ||
| etc | ||
| example | ||
| src | ||
| test | ||
| tools | ||
| .all-contributorsrc | ||
| .astylerc | ||
| .gitignore | ||
| .gitmodules | ||
| .readthedocs.yaml | ||
| CODE_OF_CONDUCT.md | ||
| codecov.yml | ||
| CONTRIBUTORS.md | ||
| LICENSE | ||
| Makefile | ||
| README.md | ||
NEWS: Our paper Occlum: Secure and Efficient Multitasking Inside a Single Enclave of Intel SGX has been accepted by ASPLOS'20. This research paper highlights the advantages of the single-address-space architecture adopted by Occlum and describes a novel in-enclave isolation mechanism that complements this approach. The paper can be found on ACM Digital Library and Arxiv.
Occlum is a memory-safe, multi-process library OS (LibOS) for Intel SGX. As a LibOS, it enables legacy applications to run on SGX with little or even no modifications of source code, thus protecting the confidentiality and integrity of user workloads transparently.
Occlum has the following salient features:
- Efficient multitasking. Occlum offers light-weight LibOS processes: they are light-weight in the sense that all LibOS processes share the same SGX enclave. Compared to the heavy-weight, per-enclave LibOS processes, Occlum's light-weight LibOS processes is up to 1,000X faster on startup and 3X faster on IPC. In addition, Occlum offers an optional PKU (Protection Keys for Userspace) feature to enhance fault isolation between Occlum's LibOS and userspace processes if needed.
- Multiple file system support. Occlum supports various types of file systems, e.g., read-only hashed FS (for integrity protection), writable encrypted FS (for confidentiality protection), untrusted host FS (for convenient data exchange between the LibOS and the host OS).
- Memory safety. Occlum is the first SGX LibOS written in a memory-safe programming language (Rust). Thus, Occlum is much less likely to contain low-level, memory-safety bugs and is more trustworthy to host security-critical applications.
- Ease-of-use. Occlum provides user-friendly build and command-line tools. Running applications on Occlum inside SGX enclaves can be as simple as only typing several shell commands (see the next section).
Occlum Documentation
The official Occlum documentation can be found at https://occlum.readthedocs.io.
Some quick links are as below.
Quick StartBuild and InstallOcclum ConfigurationOcclum Compatible Executable BinariesDemosQ & A
What is the Implementation Status?
Occlum is being actively developed. We now focus on implementing more system calls and additional features required in the production environment, including baremetal server and public cloud (Aliyun, Azure, ...) VM.
Also, a dedicated branch 1.0.0-preview is used for next generation Occlum development.
How about the Internal Working?
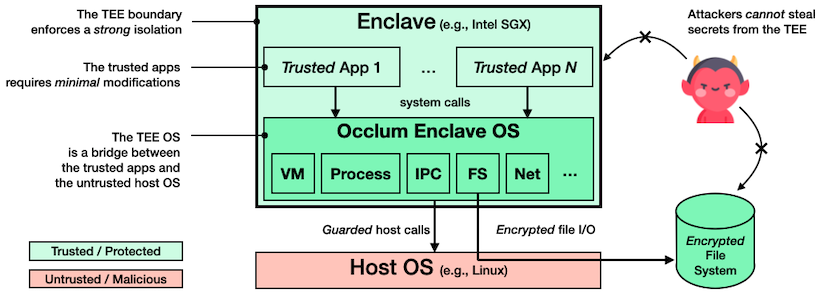
The high-level architecture of Occlum is summarized in the figure below:
Why the Name?
The project name Occlum stems from the word Occlumency coined in Harry Potter series by J. K. Rowling. In Harry Potter and the Order of Phoenix, Occlumency is described as:
The magical defence of the mind against external penetration. An obscure branch of magic, but a highly useful one... Used properly, the power of Occlumency will help shield you from access or influence.
The same thing can be said for Occlum, not for the mind, but for the program:
The magical defence of the program against external penetration. An obscure branch of technology, but a highly useful one... Used properly, the power of Occlum will help shield your program from access or influence.
Of course, Occlum must be run on Intel x86 CPUs with SGX support to do its magic.
Contributors
Contributions of any kind are welcome! We will publish contributing guidelines and accept pull requests after the project gets more stable.
Thanks go to all these wonderful contributors to this project.
License
Occlum is released under BSD License. See the copyright information here.